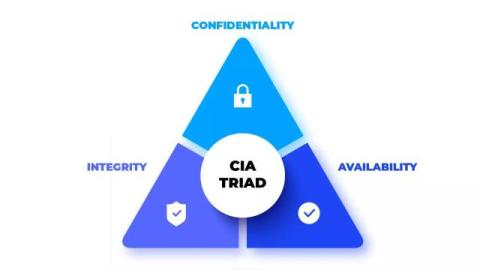
The CIA Triad: Confidentiality, Integrity, and Availability
The confidentiality, integrity, and availability (CIA) triad is a critical concept in cybersecurity, including three fundamental principles that help protect information. Organizations seeking a starting point for developing an information security framework would benefit from the triad model.