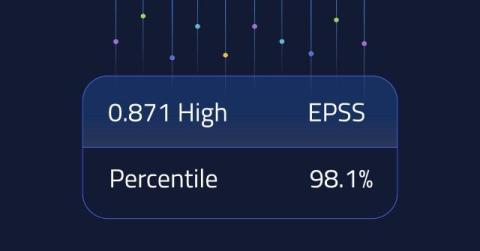
A denial of service Regex breaks FastAPI security
Welcome, fellow developers! In this blog post, we are going to delve deep into the world of application security, specifically focusing on a vulnerability that can deteriorate FastAPI security: Denial of service (DoS) caused by insecure regular expressions (regex).