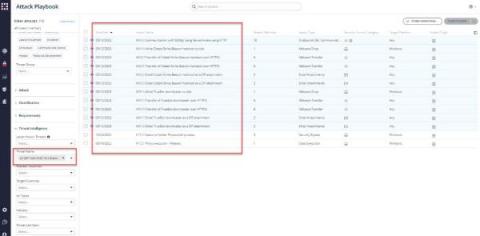
SafeBreach Coverage for US-CERT Alert (AA23-144A) - Volt Typhoon
On May 24th, the National Security Agency (NSA), the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the Canadian Centre for Cyber Security (CCCS), the New Zealand National Cyber Security Centre (NCSC-NZ), United Kingdom National Cyber Security Centre (NCSC-UK) and the Australian Cyber Security Centre (ACSC) along with their private sector partners recently discovered a cluster of activity of interest associated with a People’s Republic of China