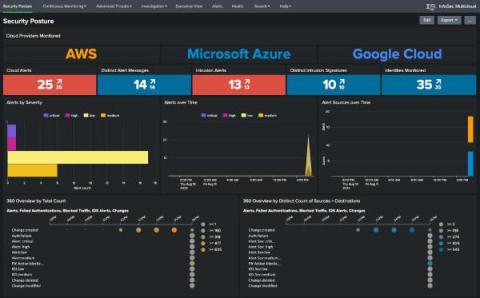
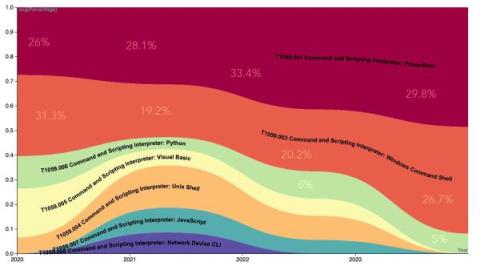
Improvements to Detecting Modern Financial Crime
Last year, we talked about different techniques for using Splunk Enterprise, Splunk Cloud Platform, and Splunk Enterprise Security to detect modern financial crime using risk scores with aggregated rules and the power of the Splunk platform.