Mergers and acquisitions insurance
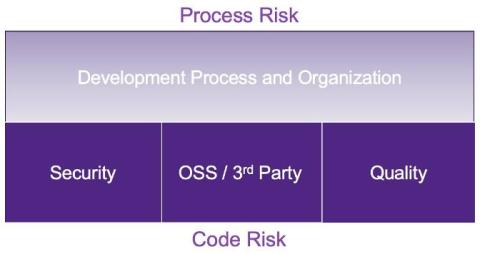
Evaluating risk is paramount in any software transaction. In the realm of mergers and acquisitions (M&As), a thorough risk assessment is essential to identify a target company’s potential pitfalls, financial liabilities, and legal obligations. The analysis of such risks is pivotal for informed decision-making, ensuring that acquirers are aware of the risks they may inherit. For insurers, risk evaluation is fundamental to establishing coverage limitations and pricing uninsurable risks appropriately.