A Microsoft SharePoint Online feature could be the cause of the next ransomware attack
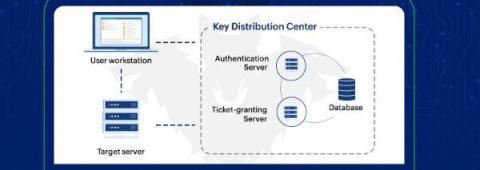
Microsoft SharePoint Online is one of the most widely used content management platforms. Unfortunately, Proofpoint recently discovered that threat actors can abuse a feature in SharePoint Online and OneDrive for Business to encrypt all of your files and hold them ransom.