Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest Blogs
Staving Off the Monetary Consequences of a Data Breach
Cybersecurity breaches and regulatory compliance are this year’s themes. Marriott was sued and fined $124 million for their data breach back in 2014, according to The Wall Street Journal. Capital One leaked 100 million credit applications including Social Security Numbers. Both LabCorp and Quest Diagnostics exposed millions of patients’ medical records.
Deepfakes are a problem, what's the solution?
Deepfakes are the latest moral panic, but the issues about consent, fake news, and political manipulation they raise are not new. They are also not issues that can be solved at a tech level. A deepfake is essentially a video of something that didn’t happen, but made to look extremely realistic. That might sound like a basic case of ‘photoshopping’, but deepfakes go way beyond this.
Simple Security Configuration Can Help Your Sensitive Data From Being Stolen
When malware sneaks inside your network, it needs to communicate back to the internet whether to exfiltrate sensitive datasets it found, accept commands of its evil masters or even simply let them know it has successfully infiltrated your infrastructure (with ransomware being one of the rare exceptions that doesn’t need such connection).
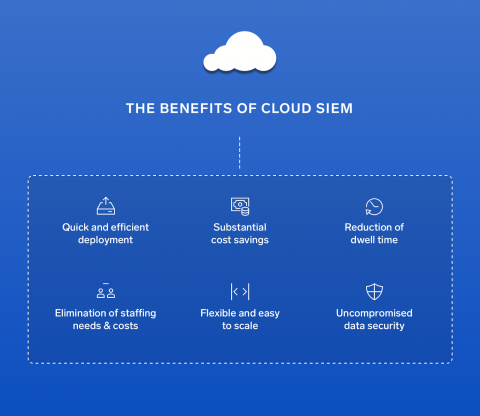
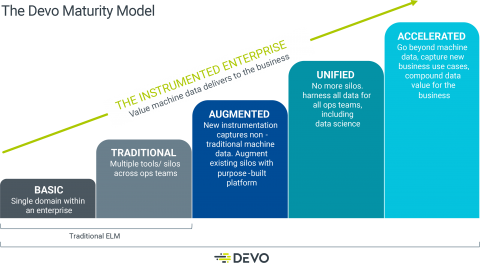
From Basic to Accelerated: The Devo Maturity Model
IDC says to estimate reaching 175 zettabytes of data by 2025, a 61 percent increase from today’s data volumes. Business leaders and IT executives overwhelmingly agree that they can do more to harness this data, but are we as an industry lacking for imagination? Or do we simply not know where to start or how to progress? To add insult to injury, today’s enterprises are stuck in the land of silos and replication, and too much data wrangling that consumes an already oversubscribed budget.
The 2019 SANS Security Awareness Report: Awareness Training Is Rising
Cybersecurity and cyber security awareness are critical to business survival in an era dominated by growing virtual crime. It might be true that most people know about costly identity theft and reputation-destroying network hacks. Organizations spend millions every year trying to defend themselves against cybercrime, but still, attacks seem to be more and more successful.
Moving to the Cloud and How You Shift Your Security Management Strategy
As someone who has worked for their entire career in the Managed Network Services space, if I had to pick out, over the past five years, two of the most impactful shifts in managing technology, it would be a shift from traditional, in-house servers to solutions where 3rd parties build “clouds” to provide similar business functions as well as the increased pressure on organizations to have comprehensive cyber-security strategies as threats become more significant.
Weekly Cyber Security News 02/08/2019
A selection of this week’s more interesting vulnerability disclosures and cyber security news. Such an amazing choice of juicy news articles this week! I will skip the seriously weird and rapidly escalating circumstances of the Capital One breach, and instead dive into the some of the more low key, but nevertheless interesting items. First up, and for those of you who post infosec articles, something you will understand: stock photos.
What Is Cybersecurity Risk? A Thorough Definition
Cybersecurity risk is the probability of a cyber attack or data breach on your organization. Organizations are becoming more vulnerable to cyber threats due to the increasing reliance on computers, networks, programs, social media and data globally. Data breaches, a common cyber attack, have massive negative business impact and often arise from insufficiently protected data.
Cyber Security Vs. Information Security: The Key Differences
While cyber security and information security are generally used as synonyms, there are key differences that need to be understood. A good place to start is with data security. Data security is about securing data. Not every bit of data is information. Data becomes information when it is interpreted in context and given meaning. An example: 061580 is data and it becomes information when we know it's a date of birth. Information is data with meaning.