Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
June 2023
Android Malware Outbreak: Unmasking the RAT Inside a Screen Recording App
With the worldwide popularity of Android and its open-source software, hackers have an increased incentive and opportunity to orchestrate attacks. A Google search for “Android malware” brings up headlines like these, all from the past few days or weeks: SecurityScorecard recently analyzed a specific threat known as the AhMyth RAT (remote access trojan), which made headlines for infiltrating a popular screen recording app on the Google Play Store.
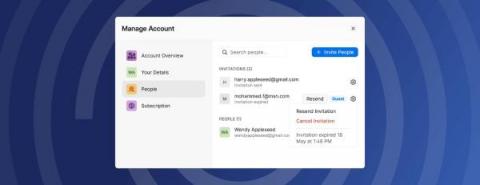
New: Manage accounts directly from the 1Password app
Coming to iOS later this week and available today on macOS, Windows, Linux, and Android, manage invites, guests, and more – all directly from the 1Password app.
New: Manage accounts directly from the 1Password app
Top tips: 8 ways to secure your mobile phones from cyberthreats
Mobile phones have become an indispensable tool in all our lives. Ensuring their security and protecting sensitive information becomes paramount, especially when you have all your work-related apps and data synced. Every 39 seconds, a new assault occurs on the internet, and 24,000 malicious mobile apps are typically blocked everyday.
Spectrum of Mobile Risk- Lookout
Understanding API Breaches: Insights from 'Outliers' and the Complexities of Cybersecurity
Over the last couple of decades in the cybersecurity industry, I have observed how APIs have gained significant importance in modern cloud-based architectures over the past few decades. In fact, they account for over 80% of all web traffic. However, this increased usage has also made APIs vulnerable to cyber threats. A closer look reveals that APIs are now one of the most prominent threat vectors in the cybersecurity landscape.
Android App Penetration Testing Checklist with 154 Test cases [Free Excel File]
How To Get Rid of Viruses From Your iPhone
Enhancing Mobile App Security through Sandboxing & Isolation
Security Testing is a crucial step in the application development process. So, how about we say you can have a dedicated environment to test your app for potential threats such that the attached malware cannot spread, access, or modify the rest of your system's files, resources, and settings? Pretty lucrative, right? Application Sandbox and isolation technique is the holy grail of application security.
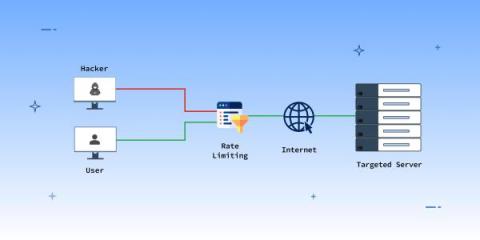
Preventing Denial of Service Attacks with Rate Limiting Techniques
A Denial of Service (DoS) attack will prevent your legitimate users from accessing your API. The attack could be physical, such as unplugging network cables, but a Distributed DoS is more prominent. It involves generating a volume of user requests from various machines to overwhelm your servers. DDoS attacks can result in a loss of $50,000 of revenue due to downtime and mitigation.
Reverse Engineering Flutter Apps: What You Need To Know?
Reverse engineering is one of the most notorious methods using which hackers exploit an application or software. If you're in the mobile app development industry and use Flutter for app development, you'd know the threat reverse engineering poses to apps. While 100% protection from reverse engineering isn't possible, you can give the hackers a tough time trying to exploit your app. And this blog is there to help.