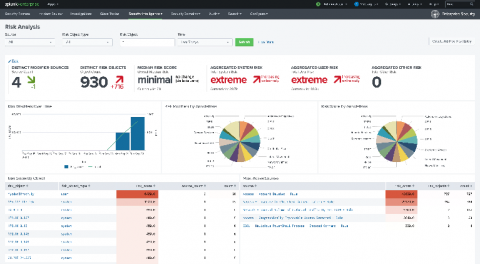
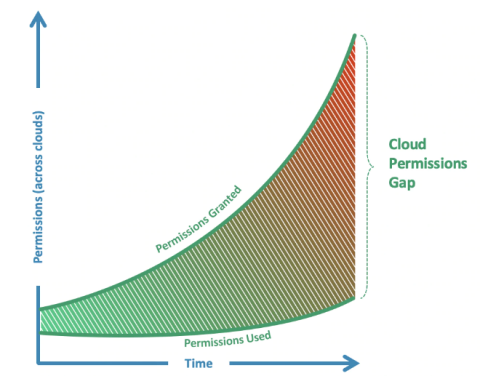
How to Define Your Security Posture, and Why it Matters
Not only do cybersecurity organizations need to deliver the level of security required to protect corporate assets, they also need to align with the strategic goals and objectives of the business. By defining, establishing and managing your organization's cybersecurity posture, you can deliver the results needed for the business to be successful.