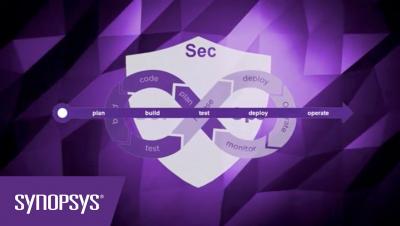
Can SAST tools improve developer productivity?
Organizations are increasingly agile today, producing and deploying software applications faster than ever before. But this requires all the elements in the software development life cycle (SDLC) to work together cohesively. Security practices in the SDLC become especially important, given that more than half of security flaws result from preventable coding mistakes. Ensuring that developers are on board with security practices is even more critical to improve the process efficiency.