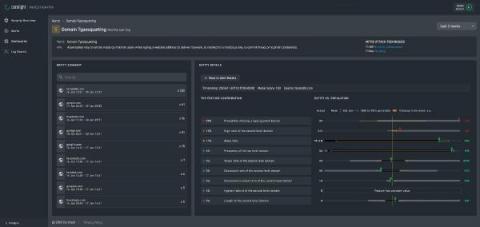
Corelight Investigator introduces new Machine Learning Models
Corelight Investigator furthers its commitment to delivering next-level analytics through the expansion of its machine learning models. Security teams are now enabled with additional supervised and deep learning models, including: We continue to provide complete transparency behind our evidence -- showing the logic behind our machine learning models and detections, allowing analysts to quickly and easily validate the alerts.