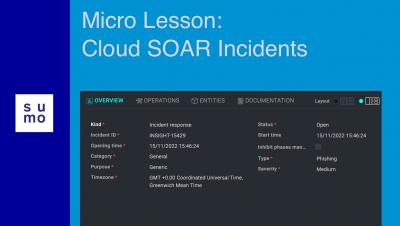
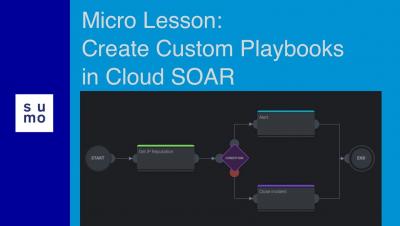
Detection notes: In-memory Office application token theft
When we hear the term “Credential Access” our detection engineer thoughts typically turn to the Windows LSASS Process and tools like Mimikatz. Recently, however, researchers have drawn our attention to Microsoft Office processes. These processes also store credential material, in the form of access tokens.