How to Secure Kubernetes Using Cloud SIEM?
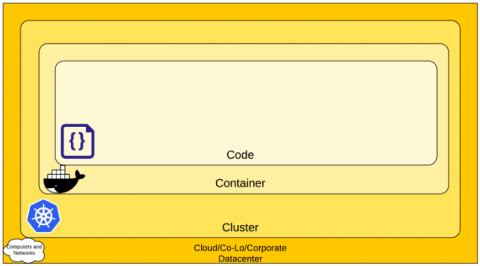
Kubernetes, commonly called K8s, is an open-source container management system developed by Google. Containers and tools like Kubernetes enable automation of many aspects of application deployment, which provides tremendous benefits to businesses. K8s is just as vulnerable to attacks and cybercrime as traditional environments, in both public and private clouds. In this blog post, we’ve compiled everything you need to know to make sure your Kubernetes environment is safe. Here is what we tackle.