Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
February 2022
6 Authentication Best Practices
Our previous blog post on authentication security covered six most common authentication vulnerabilities. In this post, we will discuss a few best practices that help avoid authentication vulnerabilities and defeat specific attack vectors. Below are the six best practices to secure the authentication process.
Teleport Your Company to IPO
One of the most exciting things about working at Teleport is getting to see how our infrastructure access solutions enable customers to grow their business. Since software has eaten the world, solutions like Teleport that enable developers to become more productive are essential to fast- growing companies. You simply can’t create a hyper growth business today without a strong software development muscle.
Lessons From Billions of Breached Records by Troy Hunt of https://haveibeenpwned.com
Most Common Authentication Vulnerabilities
The majority of threats related to the authentication process are associated with passwords and password-based authentication methods. But broken authentication also causes a significant amount of vulnerabilities. Broken authentication occurs when the implementation of the authentication process is flawed. Unfortunately, this is usually hard to discover, and can be more severe than the risks associated with passwords.
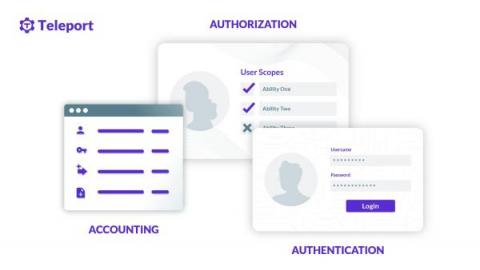
What Is AAA Security?
Authentication, authorization, and accounting, often called AAA or Triple-A, are sets of services and protocols that enable granular access control over computer networks. Before the popularity of mainstream HTTP-based authentication protocols such as OAuth and SAML, AAA protocols were the primary way to authenticate users or machines to network services.
Authentication (AuthN) and Authorization (AuthZ) Tutorial for Kubernetes
Kubernetes is an API-centric orchestration platform. Every request, from the cluster components to users interacting with the system, has to go through the API server. The API server is a component in the control plane, and acts as a gatekeeper for the operation requests originating from both inside and outside of the cluster.
Comparing Passwordless SSH Authentication Methods
There are essentially four ways you can implement passwordless SSH access. SSH certificate-based authentication, SSH key-based authentication, SSH host-based authentication, or using a custom PAM module that supports out-of-band authentication. If you want to live dangerously, there’s also a fifth method of passwordless access — disable authentication at all. But that’s not who you are!
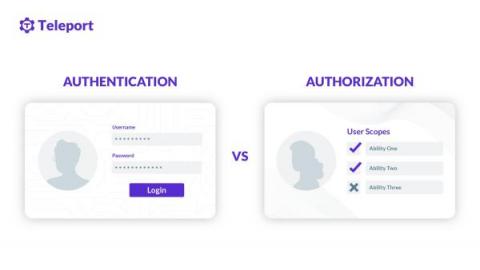
Authentication (AuthN) vs. Authorization (AuthZ)
Often referred to as AuthN (authentication) and AuthZ (authorization) in the modern access control paradigm, both authentication and authorization are a method to control access to resources. These resources can be files, programs, web applications, mobile applications, operating systems, network devices, etc. Let’s explore three common scenarios on how authentication and authorization are involved. These are the few sample cases of authentication vs. authorization.
How Teleport Uses Teleport to Create and Maintain Shared Demo Environments
Our Solution Engineering (SE) team is full of individuals who have vast real-world experience building and maintaining complex IT access systems with sophisticated audit layers through their work as DevOps engineers. The problems that we have all faced before joining Teleport are the exact problems that our customers face. So when it comes to our demos, we like to show real-world scenarios aligned to customer usage patterns, in environments similar to our customers.
How to Protect Your CI/CD Pipeline
How To Set Up SSH Keys
At Teleport, we advocate SSH certificates over SSH keys and passwords as the best authentication method for SSH. Nothing beats the security and operational flexibility of using certificate-based authentication for a large fleet of SSH servers running on dynamic infrastructure. But in practice, certificate-based authentication is far from the de facto authentication method, and sometimes we may need to use SSH keys.
Teleport: Fresh access for all your infrastructure
Using SSH Port Knocking to Hide an SSH Server
This article will explore methods for “hiding” SSH servers so that the server is harder to discover by malicious users on public networks. We’ll focus on changing the default SSH port and implementing SSH port knocking to make it more difficult for unwanted users to discover or locate the server.