Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
April 2021
When should a startup hire a CSO? Access Control #1 - Donnie Hasseltine
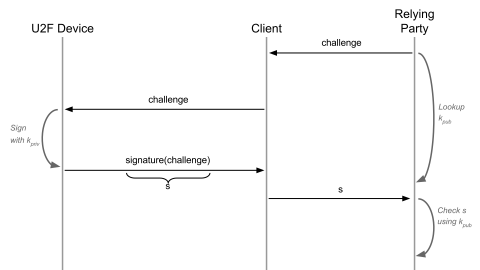
What I Wish I Knew About U2F and Other Hardware MFA Protocols
Teleport has supported multi-factor authentication (MFA) for a while now, via Authenticator Apps (TOTP) and Hardware Tokens (U2F) such as YubiKeys. But this support was pretty limited: you could only choose one MFA protocol and users could only register one device. If a user lost their device, they would be locked out and need an account reset by the administrator. So, for Teleport 6.0, we’ve reimplemented the MFA support to make it more flexible.
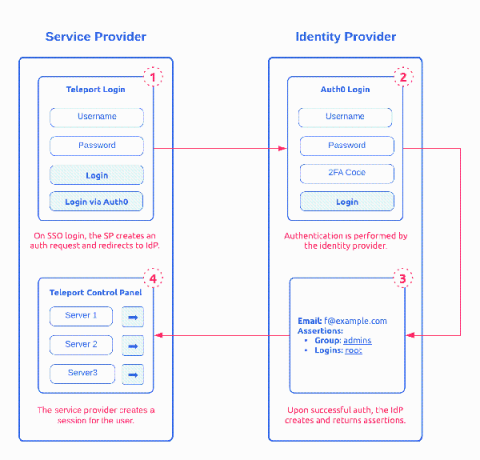
How SAML 2.0 Authentication Works?
Security Assertion Markup Language (SAML) 2.0 is one of the most widely used open standard for authentication and authorizing between multiple parties. It’s one of the protocol that give users the single sign-on (SSO) experience for applications. The other adopted open standard is OAuth and OpenID. Of the two, SAML 2.0, released in 2005, remains the 800 pound gorilla in Enterprise SSO space. This post provides a detailed introduction on how SAML works.
Teleport in 2021: Security Audit Results
We now live in an era where the security of all layers of the software stack is immensely important, and simply open-sourcing a code base is not enough to ensure that security vulnerabilities surface and are addressed. At Teleport, we see it as a necessity to engage a third party that specializes in acting as an adversary, and provide an independent analysis of our sources.
Using Google Workspace SSO with Teleport
https://goteleport.com/docs/enterprise/sso/ssh-gsuite/
0:00 Intro
0:45 Example Teleport with local login
1:12 Configure Google Workspace
3:35 Creating Service Account
5:00 Manage API Scope
6:36 Creating OIDC Connector in Teleport
10:04 tctl create gworkspace.yaml
10:13 Example Login with Google Button
Setting up Okta SSO with Teleport
0:00 Introduction
0:25 Okta Setup
0:42 Configuring Okta
3:24 Setting up Okta Groups
6:45 tctl create okta.yaml
7:16 Assigning Groups in Okta
7:41 SSO Debugging
8:50 Conclusion
Securing Your PostgreSQL Database
Databases are the Holy Grail for hackers, and as such, must be protected with utmost care. This is the first in a series of articles in which we’ll give an overview of best practices for securing your databases. We’re starting with one of the most popular open-source databases, PostgreSQL, and will go over several levels of security you’d need to think about.