Container Drift Detection with Falco
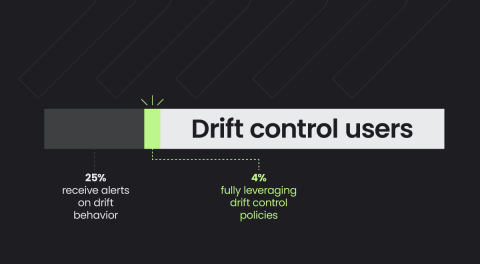
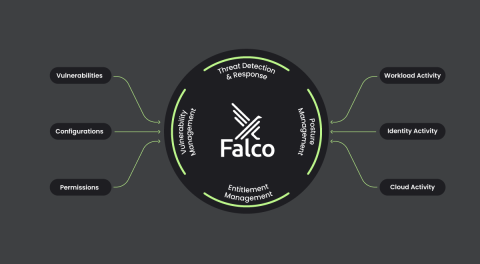
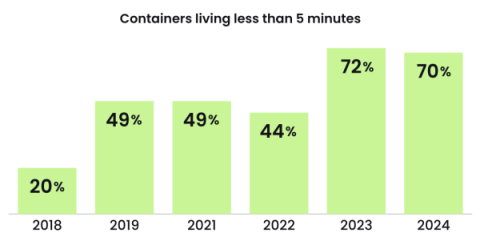
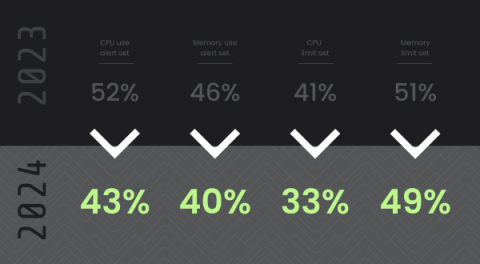
DIE is the notion that an immutable workload should not change during runtime; therefore, any observed change is potentially evident of malicious activity, also commonly referred to as Drift. Container Drift Detection provides an easy way to prevent attacks at runtime by simply following security best practices of immutability and ensuring containers aren’t modified after deployment in production.