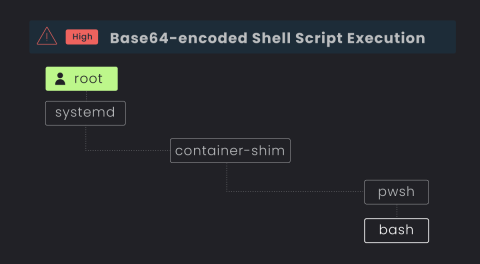
The Power of Library-Based Vulnerability Detection.
With an ever-growing number of vulnerabilities being discovered annually, vulnerability management tools are rapidly evolving to handle and prioritize these risks. However, it remains one of the most overwhelming and time-consuming areas in cybersecurity. There’s still significant room for enhancement, especially in reducing false alerts and prioritizing genuine threats.