Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
The PwnKit vulnerability: Overview, detection, and remediation
On January 25, 2022, Qualys announced the discovery of a local privilege escalation vulnerability that it identified as PwnKit. The PwnKit vulnerability affects PolicyKit’s pkexec, a SUID-root program installed by default on many Linux distributions. The same day of the announcement, a proof of concept (PoC) exploit was built and published by the security research community.
Detecting and mitigating CVE-2021-4034: "Pwnkit" local privilege escalation
A new advisory from Qualys discloses a local privilege escalation bug in SUID-set program ‘pkexec’. The flaw has been designated the CVE ID of CVE-2021-4034 and nicknamed “pwnkit” by the vulnerability finders. The CVSSv3 base score is calculated to be a high 7.8 out of 10.0. The vulnerable program is a part of Polkit, which manages process privileges.
CVE-2020-0696 - Microsoft Outlook Security Feature Bypass Vulnerability
During an investigation of a malware campaign, I discovered that multiple emails were bypassing a specific email security system. Interestingly, there were no bypass techniques used. Instead, the flood of spear-phishing emails made the email security system allow some of the emails, at which point I began my research on Microsoft Outlook. The issue in this case was that the specially crafted malicious link parsing on the security system was weak.
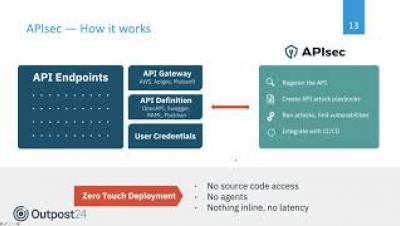
Outpost24 Webinar - API security 101 and how to secure your web applications
CVE-2021-4034: A Walkthrough of Pwnkit - the Latest Linux Privileges Escalation Vulnerability
Since 2009, more than 12 years ago, all major Linux distributions have been incorporating a high severity security hole that remained unnoticed until just recently. The vulnerability and exploit, dubbed “PwnKit” (CVE-2021-4034), uses the vulnerable “pkexec” tool, and allows a local user to gain root system privileges on the affected host. Polkit (formerly PolicyKit) is a component for controlling system-wide privileges in Unix-like operating systems.
Press information: Detectify sees significant increase in detected vulnerabilities powered by its Crowdsource community
“Crowdsourced security provides a way for security teams to expand their efficiency, especially when it comes to managing their external attack surface,” said Rickard Carlsson, Co-founder and CEO of Detectify. “Hackers have eyes and ears all over the web, and they’re constantly monitoring attack surfaces for exploitable entry points.
Log4Shell in the Field - A Brief Analysis Through January 2022
Vulnerability of the Month: nanoid
Trustwave Threat Hunting Guide: Identifying PwnKit (CVE-2021-4034) Exploitation
The Trustwave Threat Hunting team has authored a practical guide to help the cybersecurity community address the Linux “polkit” Local Privilege Escalation vulnerability (CVE-2021-4034) by identifying common behavior in exploitation.