Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
CVE-2022-1271 - Improper Input Validation in Gzip | Synopsys
CVE-2022-24675 - Stack overflow (exhaustion) in Go's PEM decoder
A few days ago it was reported that the new Go versions 1.18.1 and 1.17.9 contain fixes for a stack overflow vulnerability in the encoding/pem builtin package, in the Decode function. Given the high popularity of Go among our customers and in the industry at large, this update led us to investigate the vulnerability in previous versions.
Top 7 Vulnerability Mitigation Strategies
An unintimidating introduction to the dark arts of C/C++ vulnerabilities
As Synk announces its support of unmanaged dependencies (mostly C/C++ libraries), we thought it would be beneficial to introduce our non-C community to some common, high-risk dangers that lurk in the C world (get it?). Think of this as a “beginners guide” to C and C++ vulnerabilities, how they look, what problems they may cause, and how to fix them.
'Hackad' hacker: CISOs have more to worry about than a zero day exploit
When I look at IT security I can clearly see how it has changed, being today much more mature now than it’s ever been. Governments are working on policies and legislation forcing companies to prioritize IT security. As a result, the entire bug bounty community has bloomed in a way that I could never imagine, security researchers are now working together with companies to identify and mitigate vulnerabilities in a way that we have never done before.
Wormable Vulnerability in Windows Remote Procedure Call (RPC) - CVE-2022-26809
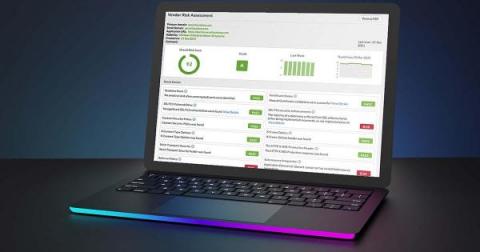
Trustwave Security Colony Vendor Assessment: Know Your Vulnerabilities Before Others Do
This is the second installment in Trustwave’s in-depth tour of our Security Colony platform. For a broad overview of what Security Colony offers please read 5 Ways CISOs Can Leverage the Power of Trustwave Security Colony. Self-evaluation in any area, much less cybersecurity, can be challenging. Is my performance at work strong and consistent? Am I being friendly to my neighbors?