Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
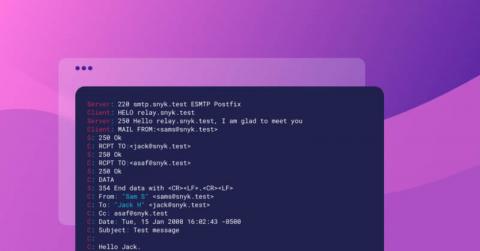
Avoiding SMTP Injection: A Whitebox primer
SMTP Injection vulnerabilities are often misunderstood by developers and security professionals, and missed by static analysis products. This blog will discuss how common SMTP Injection vulnerabilities can exist in libraries and applications, and provide tips for finding and remediating them quickly.
Announcing the 2022 State of Cloud Security report from Snyk
Cloud computing has created the most profound shift in information technology in recent memory. Leveraging cloud technology, companies can build, deploy, and scale their applications faster than ever. But the adoption of cloud native tools and processes also brings new security challenges. Between complex cloud infrastructure and the expansion of cloud-based services, malicious actors have access to a bigger attack surface than they did even a few years ago.
The importance of application security: keeping your web apps safe
Web application security is crucial for any organization that relies on web-based applications. Learn about the importance of web application security and best practices for keeping your organization safe. The importance of web application security cannot be overstated. As organizations move towards web-based applications and services to run their business and connect with customers, it is becoming more vital than ever to secure those systems from malicious attacks.
How Spotify uses Snyk to secure the SDLC
Spotify’s engineering team recently published a blog discussing their use of Snyk to maintain security testing in the SDLC. The following is a recap of that blog written by Engineering Manager, Edina Muminovic. Spotify, a company known for employing thousands of world-class developers, needed to redraw its software development lifecycle, or SDLC.
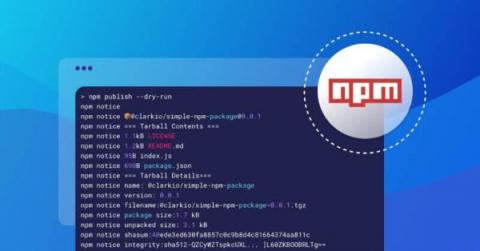
Best practices for creating a modern npm package
Technology is always changing and your processes and practices need to keep up with those changes. So while npm is 12 years old, your practices around npm package creation should hopefully be a lot more modern. If you have a feeling they may be a little out of date, though, keep reading.
How Onna Technologies uses Snyk & Sysdig to secure the SDLC while saving time and money
Onna Technologies, a data centralization software company, integrates security across every facet of their development process by using Snyk and Sysdig. We recently sat down with Onna’s Brent Neal (Director of Security), Mike Hoffman (Lead Security Engineer), and Andrew Leeb (Senior Software Engineer) to discuss data protection and compliance, cloud security priorities, and the benefits using Snyk and Sysdig for complete end-to-end container security.
OWASP Verification Standard: Application Security and Standards
At the beginning of August, CREST partnered with OWASP to release the OWASP Verification Standard (OVS), which is designed to formalise and expand on OWASP’s existing work on application security and their own security standards, including their Top 10 Project. OWASP has existed since December 2001 and has been supporting penetration testers and developers alike ever since with tens of thousands of participants.
De-risking Code with Snyk and Codecov
Using Kubernetes ConfigMaps securely
ConfigMaps is an API object used in Kubernetes to store data in key-value pairs. It’s essentially a dictionary that contains configuration settings. Some details you might expect to find in a ConfigMap include hostnames, public credentials, connection strings, and URLs. A ConfigMap decouples an application’s code from the configurations, making it possible to alter them without impacting the application.