Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Vulnerability
AppSec Decoded: Takeaways from the 2022 "Software Vulnerability Snapshot"report | Synopsys
Vulnerability Causing Deletion of All Users in CrushFTP Admin Area
During a recent penetration test, Trustwave SpiderLabs researchers discovered a weak input validation vulnerability in the CrushFTP application which caused the deletion of all users. CrushFTP is a secure high- speed file transfer server that runs on almost any OS. It handles a wide array of protocols, and security options. CrushFTP stores details of registered users within the filesystem in the users/MainUsers directory.
CVE-2022-27596: QNAP NAS Devices Vulnerable to Critical SQL Injection Vulnerability
4 application security bad habits to ditch in 2023 (and best practices to adopt instead)
Regardless of how last year went, a few things probably come to mind that you’d like to leave in 2022. Maybe it’s a bad habit you’d like to drop or a mindset you’d like to change. But speaking of ditching bad habits, some poor cloud application security practices shouldn’t carry over to 2023 either!
4 Categories of Container Security Vulnerabilities (& Best Practices to Reduce Risk)
Containerization is becoming increasingly common due to portability, ability to isolate application dependencies, scalability, cost effectiveness, and ease of use. The ability to easily package and deploy code has changed the way that organizations work with applications. But like with Windows servers years ago, or AWS today, any time one specific technology gains a significant portion of the market share, it becomes a target for attackers.
CTI Roundup: Threat Actors Use Sliver C2 Framework
Sliver’s growing popularity as an open-source C2 framework, Emotet’s comeback and new evasion techniques, and how Chinese hackers exploited a Fortinet flaw using a 0-Day.
Stranger Danger: Your JavaScript Attack Surface Just Got Bigger
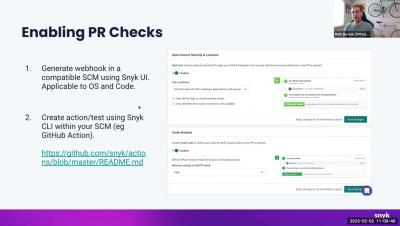
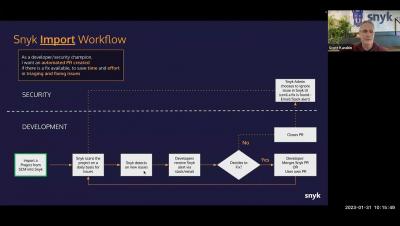
Snyk Workflows - Basic Workflows (IDE & CLI)
When is the right time for vulnerability scanning?
All it takes for cybercriminals to breach your mission-critical networks, database, and IT systems is a single unpatched vulnerability. To prevent this and maintain good cyber hygiene, you need to obtain real-time vulnerability data. Vulnerability scans generate a lot of data that when analyzed reveal several security flaws.