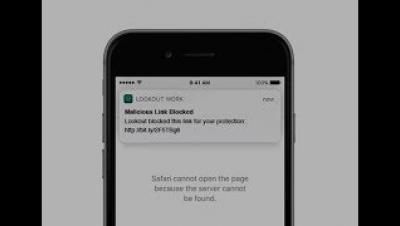
Google takes a bold step toward securing your Gmail, but not without many complaints
Many Gmail users were recently greeted with a message that alerted them that 2-step verification will be required to log into their accounts starting on November 9th (today). While many in the security community have been advising people to turn on 2-factor, 2-step, or any other secondary security method on every account as a way to protect the login process, the Twitterverse showed that many people were unhappy with Google’s implementation of this mandatory change.