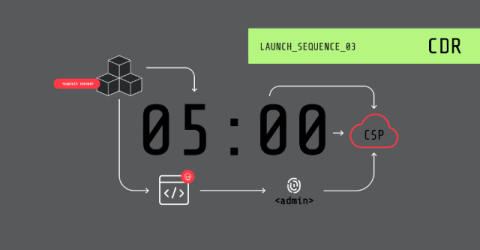
How to Cut Cloud Investigations to 5 Minutes with Sysdig
Cloud breaches continue to rise unabated as organizations adopt hybrid cloud strategies. Many organizations have tried to simply extend their preexisting on-premises security into the cloud, but the cloud is a fundamentally different environment for security. It’s faster, more complex, and more dynamic, with an ever-increasing attack surface. Striking first means adversaries have a head start by default, leaving organizations only a fraction of time to investigate and initiate a response.