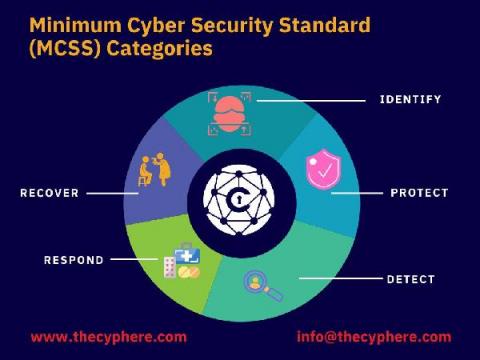
The most popular cyber security standards in UK
There are many information security standards that UK businesses can work with to protect themselves from cyber related risks. If you’re looking for straightforward measures, which will provide a great starting point and demonstrate compliance in the industry, don’t fret!