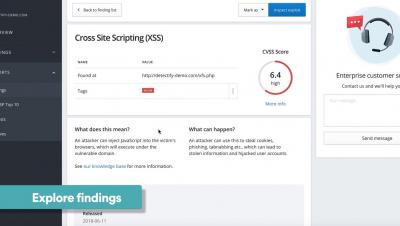
Top 10 PCI DSS Compliance Pitfalls
Despite the fact that PCI DSS has been in effect for over a decade, and most merchants are achieving compliance, some of the world’s largest retailers have been hit by to data breaches. The sad truth is that achieving compliance doesn’t guarantee data protection, even for large organizations. For example, more than five million credit card numbers were stolen in 2018 hacks of two major retailers.