Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
JFrog
DevOps Speakeasy with Tracy Ragan
Introducing JFrog Curation
Addressing the npm Manifest Confusion Vulnerability
A potential security risk in the npm ecosystem known as “manifest confusion” has recently been spotlighted in a blog post by Darcy Clarke, a former Staff Engineering Manager at GitHub. Clarke mentioned that JFrog Artifactory seems to replicate this issue, so of course we investigated it right away. In this post, we will explain what the issue is and what it might mean for JFrog Artifactory users.
Defend Your Software Supply Chain by Curating Open-Source Packages Entering Your Organization | Announcing JFrog Curation
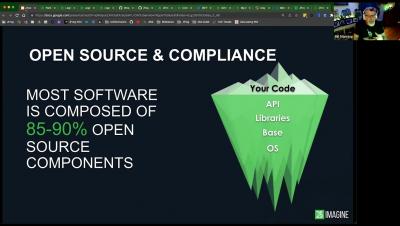
Modern organizations are constantly striving to gain a competitive advantage by delivering software solutions at a remarkable pace. To achieve this, they heavily rely on open-source software (OSS) libraries and packages, which constitute a significant portion (80-90%) of their software solution. However, while open-source software offers numerous benefits, it also presents potential security challenges.
Prevent Credential Exposure in Code
In today’s software development world, developers rely on numerous types of secrets (credentials), to facilitate seamless interaction between application components. As modern applications become more complex and require authentication for services and dependencies, the practice of hardcoding secrets during software development is on the rise.
How to Spend Less Time Fixing CVEs
Securing Your Software Supply Chain with JFrog and Azure
Three approaches to strengthening security with allowlists
There are many ways bad actors try to infiltrate and exploit companies, including by gaining access to your internal network and the applications connected to it. With more organizations adopting products in the cloud, or at the very least connected to the internet, addressing this potential attack vector is an important element of any security strategy.
JFrog and Atlassian simplify DevOps-Centric security
Atlassian has long been helping agile teams collaborate, track progress, and manage projects more efficiently, and is now simplifying software security for Jira Software Cloud users. We’re excited to announce that JFrog has joined Atlassian as a security partner.