Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Tigera
A majority of existing workloads are non-Kubernetes, and for the platform teams involved, this creates challenges because the cluster will need to be securely connected to those resources. Calico Enterprise includes several features that enable fine-grained access controls between your microservices and databases, cloud services, APIs, and other applications that may be protected behind a firewall. There are different approaches to managing Kubernetes egress access, depending on your needs and where you want the control point to be
Deploying Calico in Your On-prem Kubernetes Cluster: Networking and Security Considerations
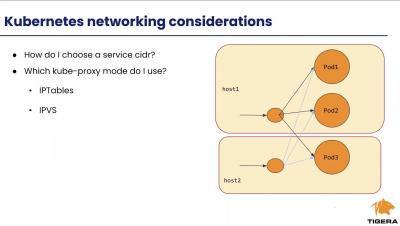
If you are deploying Kubernetes on-premises in your datacenter, this is a talk and demo you won’t want to miss. Networking and security might not be the first things that come to mind, but without some understanding of the networking and security decisions you’ll need to make, and the right options for your environment, you’re likely to get stuck or make the wrong assumptions. These may limit your ability to scale or integrate with the rest of the datacenter network.
Multi-Cluster, Multi-Cloud and Hybrid Cloud Networking, Observability and Security Management
Managing networking, observability and security in multiple Kubernetes clusters can quickly become a major challenge. Lack of a centralized, unified multi-cluster approach results in dozens of clusters that are deployed and managed independently throughout an organization, with very little uniformity in the way they are secured. This adds complexity for DevOps teams, who must adapt to different cluster environments.
Extending Your Fortinet FortiManager to Kubernetes
Tigera and Fortinet have joined forces to solve this operational challenge. With the combination of FortiManager and Calico Enterprise, you gain access control and full visibility into the container environment along with centralized management. In this webinar, you will learn how Calico Enterprise and FortiManager enable you to.
Extend Your Fortinet FortiManager to Kubernetes
Companies are leveraging the power of Kubernetes to accelerate the delivery of resilient and scalable applications to meet the pace of business. These applications are highly dynamic, making it operationally challenging to securely connect to databases or other resources protected behind firewalls.
Calico and K8s Network Policies - An Overview and Comparison
In an age where attackers are becoming more and more sophisticated, network security as a line of defense is more important than ever. Network Policy is the primary tool for securing a Kubernetes network. It allows you to easily restrict the network traffic in your cluster so only the traffic that you want to flow is allowed. In this training session, we will go over the core concepts in Kubernetes Network Policies and Calico Network Policies. Compare and contrast between the two models, and highlight when to use one versus the other.
Secure Networking for Openshift
The Kubernetes network model defines a flat network in which pod connectivity is unimpeded, with no restrictions on what traffic is allowed to or from each pod. To make a cluster production ready you need to make this networking secure. Network Policy is the primary tool for doing this and is essential to understand before considering moving a cluster to production.
Kubernetes Q3-2020: Threats, Exploits and TTPs
Kubernetes has become the world’s most popular container orchestration system and is taking the enterprise ecosystem by storm. At this disruptive moment it’s useful to look back and review the security threats that have evolved in this dynamic landscape. Identifying these threats and exploits and being a proactive learner may save you a lot of time and effort…as well as help you retain your reputation in the long run.
Network Policy with GKE
By default, pods are non-isolated; they accept traffic from any source. The Google GKE solution to this security concern is Network Security Policy that lets developers control network access to their services. Google GKE comes configured with Network Security Policy using Project Calico which can be used to secure your clusters. This class will describe a few use cases for network security policy and a live demo implementing each use case.
How to Secure Mixed Linux/Windows Clusters with Calico Policy
Calico is the only cross-platform CNI and Network Policy engine available today and is currently powers more than 150,000 known clusters across millions of nodes worldwide. Many organizations have .NET and windows workloads that they are or will eventually modernize and deploy to Kubernetes. We have been collaborating with Microsoft and joint customers over the past few years to bring Calico to the Windows platform.