Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Tigera
Network Security for D2iQ Konvoy
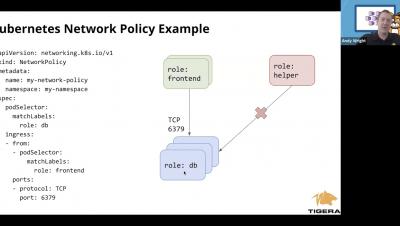
How to Implement Network Policy in Google GKE to Secure Your Cluster
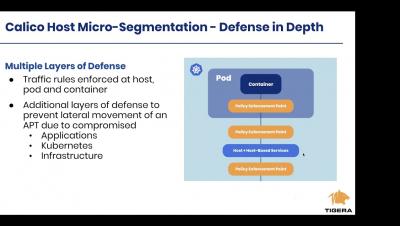
Getting up and running with Calico Host Micro segmentation Protection on AWS
Calico Enterprise 3.0 - Global Network Security Center for Kubernetes
As our enterprise customers build out large, multi-cluster Kubernetes environments, they are encountering an entirely new set of security challenges, requiring solutions that operate at scale and can be deployed both on-premises and across multiple clouds.
How to Implement Network Policy in Azure AKS to Secure Your Cluster
How to Implement Network Policy in Amazon EKS to Secure Your Cluster
Kubernetes Threat Intelligence: Detecting Domain Generation Algorithms (DGA)
Why use Typha in your Calico Kubernetes Deployments?
Calico is an open source networking and network security solution for containers, virtual machines, and native host-based workloads. Calico supports a broad range of platforms including Kubernetes, OpenShift, Docker EE, OpenStack, and bare metal. In this blog, we will focus on Kubernetes pod networking and network security using Calico. Calico uses etcd as the back-end datastore. When you run Calico on Kubernetes, you can use the same etcd datastore through the Kubernetes API server.