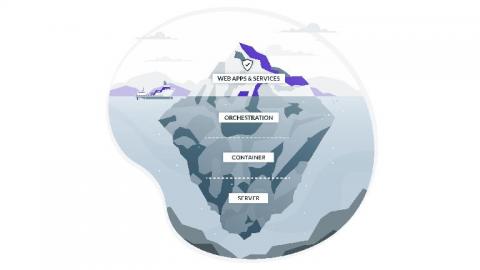
Microservices, Containers and Kubernetes in 10 minutes
What is a microservice? Should you be using microservices? How are microservices related to containers and Kubernetes? If these things keep coming up in your day-to-day and you need an overview in 10 minutes, this blog post is for you. Fundamentally, a microservice is just a computer program which runs on a server or a virtual computing instance and responds to network requests.