Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Teleport
Adding your first server to Teleport
Access Control #3: State of Startup Application Security
Teleport Cloud in 2021: Security Audit Results
This year we launched Teleport Cloud, a new service for providing a hosted version of Teleport Access Plane. One of the first problems the team had to tackle was how to secure the new infrastructure properly, and the team wanted to ensure the best possible results by engaging in an independent audit. As with the Teleport core product, we engaged with Doyensec to provide an independent security audit of our production environment.
Pull Requests for Infrastructure Access
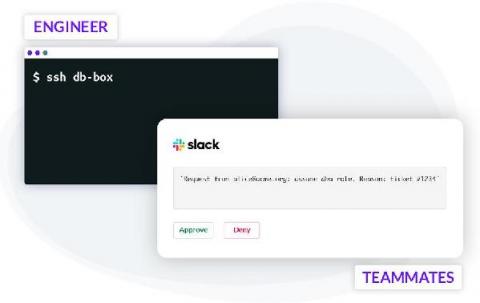
Making frequent changes to cloud applications running in production is the de-facto standard. To minimize errors, engineers use CI/CD automation, techniques like code reviews, green-blue deployments and others. Git pull requests often serve as a foundational component for triggering code reviews, Slack notifications, and subsequent automation such as testing and deployments. This automated process enforces peer reviews and creates enough visibility to minimize human error.
Secure Session Transfer Between Web Apps on Different Domains
Writing a web application that supports securely logging into a website and managing your credentials is a surprisingly difficult task. You have to develop a way to manage sessions, understand how browsers store state (cookies), learn a cryptographically safe password storing technique (like bcrypt), all the while making sure you mitigate common web security vulnerabilities like XSS and CSRF.