Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Forescout
Forescout Wins IoT Security Solution of the Year Award
It’s with great pleasure that we announce that Forescout has been awarded with “Overall IoT Security Solution of the Year” for our Forescout Continuum Platform in the 6th annual CyberSecurity Breakthrough Awards. This is the second consecutive year Forescout has been an award recipient in the CyberSecurity Breakthrough Awards in recognition of the support we offer to our customers and the larger cybersecurity industry.
Meet Vedere Labs
Holistic Cybersecurity for Government IT/IoT/OT Converged Networks
Government agencies rely on IoT and OT devices to carry out their missions and manage everything from security cameras and personal identity verification (PIV) card readers that monitor and control access to facilities and data, to environmental controls that improve comfort, safety and efficiency. Data centers couldn’t operate around the clock without tightly controlled air conditioning, electricity and other physical infrastructure, much of which relies on IoT.
Zero Trust
FBI Notice Underscores Cyberthreats Posed by Medical Devices and IoMT - Risk Management Can Help
On September 12, the FBI released a private industry notification entitled “Unpatched and Outdated Medical Devices Provide Cyber Attack Opportunities.” The notification underscores how a growing number of vulnerabilities in medical devices and Internet of Medical Things (IoMT) assets can be exploited by threat actors to “impact healthcare facilities’ operational functions, patient safety, data confidentiality and data integrity.”
How Hospital Hacks Happen: The Unmanaged Digital Terrain
How Hospital Hacks Happen: Internal Access Points
Ransomware Trends in 2022H1: State-Sponsored Ransomware, New Popular Targets and Evolving Extortion Techniques
Throughout the first half of 2022, Vedere Labs published analyses of prominent ransomware families, such as Conti, Night Sky and ALPHV. We also examined well-known ransomware incidents such as the attacks on the NFL’s SF 49ers by the BlackByte group; on a UK water utility, where the Clop gang managed to access their SCADA system; and on an NHSsoftware provider, where an unknown group managed to disrupt healthcare services in the UK for weeks.
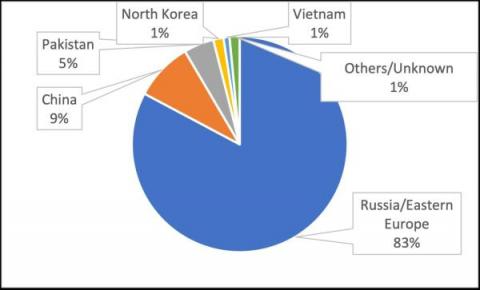
Cyberthreat Trends in 2022H1: Threat Actors Observed, New Malware and Active Hacking Groups
In our companion blog post, Vedere Labs analyzed the main ransomware trends we observed in the first half of 2022, including state-sponsored ransomware, new mainstream targets and evolving extortion techniques. Ransomware is the main threat targeting most organizations nowadays. However, three other notable cyberthreat trends also evolved during this period: Below we analyze each of these trends in more detail.