Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
CrowdStrike
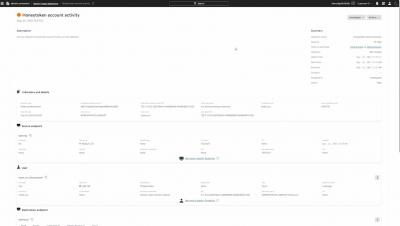
Falcon Identity Protection Risk-based Conditional Access: Demo Drill Down
The Windows Restart Manager: How It Works and How It Can Be Hijacked, Part 1
Malware utilizes a multitude of techniques to avoid detection, and threat actors are continuously uncovering and exploiting new methods of attack. One of the less common techniques includes the exploitation of the Windows Restart Manager. To stay ahead of malicious authors, it is important to be aware of them and understand how they work.
Amid Sharp Increase in Identity-Based Attacks, CrowdStrike Unveils New Threat Hunting Capability
Adversaries are doubling down on identity-based attacks. According to Nowhere to Hide: CrowdStrike 2023 Threat Hunting Report, we’ve seen an alarming 583% year-over-year increase in Kerberoasting attacks — a form of identity-based threat — and a 147% increase in access broker advertisements on the dark web. Adversaries are evolving their tradecraft, building custom tooling and leveraging more than usernames and passwords to breach your environments.
Healthcare Is Experiencing a Cybersecurity Emergency
Hospitals are seeking creative ways to fund technology and cybersecurity protection measures amid a perfect storm of operational challenges that affect quality of care.
CrowdStrike Falcon LogScale Demo
CrowdStrike's Solution to Help School Districts Meet Cybersecurity Challenges
IT administrators and security teams are back to school and busy preparing for new students and new challenges. Technology is now an integral part of K-12 education — since the pandemic, ChromeOS devices like Chromebooks have revolutionized the learning experience, enabling students and educators to access a wealth of resources and collaborate seamlessly from almost anywhere, evolving the way students learn and teachers teach.
Three Ways to Enhance Your Cloud Security with External Attack Surface Management
The IT future is a cloudy one. Organizations are increasingly relying on cloud servers, as today’s IT environments use a combination of public and private clouds alongside on-premise infrastructure. Gartner® estimates that by 2026, 75% of organizations will adopt a digital transformation model predicated on the cloud as the fundamental underlying platform.