Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
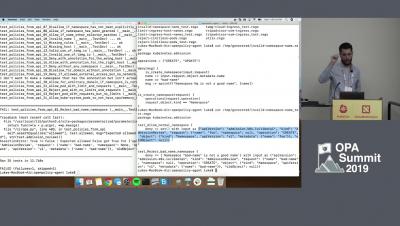
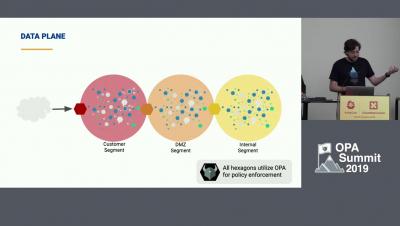
Deploying Open Policy Agent at Atlassian
Open Policy Agent for Policy-enabled Kubernetes and CICD
17 Ransomware Examples
Ransomware, a type of malicious software or malware, is designed to deny access to computer systems or sensitive data until ransom is paid. While ransomware has been around for decades, ransomware attacks are becoming more sophisticated, spreading through phishing emails, spear phishing, email attachments, vulnerability exploits, computer worms and other attack vectors.
What is Fileless Malware?
PSA: Beware of Exposing Ports in Docker
Docker is an awesome technology, and it’s prevalent in nearly every software developer’s workflow. It is useful for creating identical environments and sharing them between development, testing, production, and others. It’s a great way to ship a reliable software environment between systems or even to customers. However, like with any technology, one must know how to be secure when using it.
What is Sextortion?
What is Sextortion? Sextortion is a way of criminally extorting money from a victim or forcing the victim to carry out an act unwillingly. More often than not, the attacker threatens to publicly release embarrassing, personal images or video footage of the victim. Pornographic blackmail is commonly the angle used in sextortion.
The New Sumo Logic AWS Security Quick Start
What is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework provides a framework, based on existing standards, guidelines and practices for private sector organizations in the United States to better manage and reduce cybersecurity risk. In addition to helping organizations prevent, detect and respond to cyber threats and cyber attacks, it was designed to improve cybersecurity and risk management communications among internal and external stakeholders. The framework is increasingly adopted as best practice, with 30% of U.S.