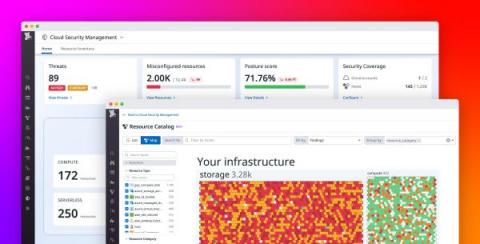
Add security context to observability data with Datadog Cloud Security Management
Organizations are rapidly migrating their infrastructure to the cloud, enabling them to modernize their applications and deliver more value to their customers. But this transition creates significant security risks that they may be unable to keep pace with. For example, cyber attacks on cloud resources are becoming more sophisticated and prevalent. Additionally, organizations often rely on legacy, disjointed security tools that don’t integrate well with cloud-native infrastructure.