Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Go
How to Handle Secrets in Go
CherryLoader: A New Go-based Loader Discovered in Recent Intrusions
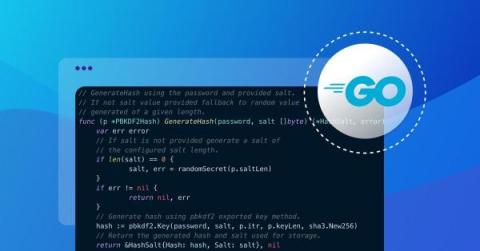
Secure password hashing in Go
User credentials are the information required to authenticate a user's identity and grant them access to a system or application. Typically, this includes a username or email address and a password. While a username can be stored as plaintext in a database, sensitive information like email addresses or passwords should not. If a malicious actor gains access to your database where you store this information, you don't want to hand over this information to them easily.
A Rash of Recent CVEs in Go
At 12 years old, Go is a relatively new programming language–but it’s a popular one when it comes to cloud-native computing. CockroachDB, Docker, Kubernetes, and AdGuardHome (byAdGuard) are all built on Go, and the Go GitHub repository has over 105,000 stars, putting it in third place as a GitHub star leader.
Improvements in Go Fuzzing (Golang 1.19)
Golang was the first programming language to support fuzzing as a first-class experience in version 1.18. This made it really easy for developers to write fuzz tests. Golang 1.14 introduced native compiler instrumentation for libFuzzer, which enables the use of libFuzzer to fuzz Go code. libFuzzer is one of the most advanced and widely used fuzzing engines and provides the most effective method for Golang Fuzzing.
CVE-2022-24675 - Stack overflow (exhaustion) in Go's PEM decoder
A few days ago it was reported that the new Go versions 1.18.1 and 1.17.9 contain fixes for a stack overflow vulnerability in the encoding/pem builtin package, in the Decode function. Given the high popularity of Go among our customers and in the industry at large, this update led us to investigate the vulnerability in previous versions.
Best practices for containerizing Go applications with Docker
Containerization describes the creation of a self-contained computing environment that runs on a host machine and any operating system (OS) with an available container runtime engine. Built from an image, a container holds an app and the filesystem alongside configurations, dependencies, binaries, and other specifications needed to run it successfully. Containers are typically much smaller than virtual machines and run in the host’s OS rather than containing OSs themselves.
How to set up a Private, Remote and Virtual Go Registry
The simplest way to manage and organize your Go dependencies is with a Go Repository. You need reliable, secure, consistent and efficient access to your dependencies that are shared across your team, in a central location. Including a place to set up multiple registries, that work transparently with the Go client. With the JFrog free cloud subscription, including JFrog Artifactory, Xray and Pipelines, you can set up a free local, remote and virtual Go Registry in minutes.
Best Go Regex Library
Skip below to the results, otherwise read on to learn more about our specific use case.