The role of DDI solutions in optimizing educational network infrastructures
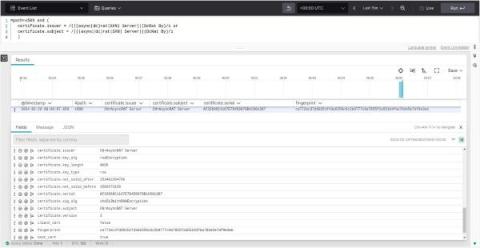
In an age where education extends beyond the four walls of classrooms and spills into the digital landscape, the security of educational institutions’ networks is not just a concern; it is a critical priority. The diverse user groups, ranging from young learners in K-12 to those in academia, all interact within the same digital infrastructure, making it a vibrant yet vulnerable ecosystem.