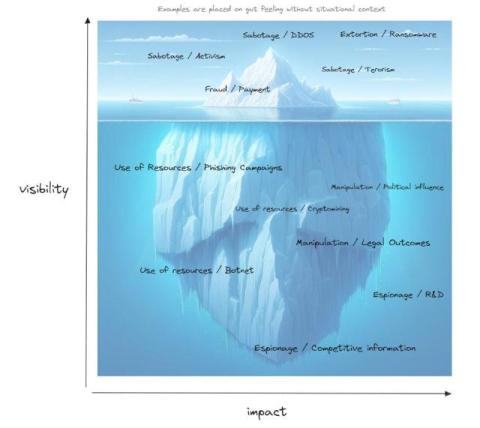
Woken by Ransomware, Are We Hypnotized by Tunnel Vision?
Over the last five to ten years cybersecurity has become a boardroom subject in the majority of enterprises. This would have never happened without ransomware. Ransomware has been the best board-level awareness tool ever.