Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Logging
OWASP Top 10 in 2021: Security Logging and Monitoring Failures Practical Overview
Security Logging and Monitoring Failures is #9 in the current OWASP top Ten Most Critical Web Application Security Risks.
Why Midsized SecOps Teams Should Consider Security Log Analytics Instead of Security and Information Event Management
How Cloudflare Logs Provide Traffic, Performance, and Security Insights with Coralogix
Cloudflare secures and ensures the reliability of your external-facing resources such as websites, APIs, and applications. It protects your internal resources such as behind-the-firewall applications, teams, and devices. This post will show you how Coralogix can provide analytics and insights for your Cloudflare log data – including traffic, performance, and security insights.
Security Log Management Done Right: Collect the Right Data
Nearly all security experts agree that event log data gives you visibility into and documentation over threats facing your environment. Even knowing this, many security professionals don’t have the time to collect, manage, and correlate log data because they don’t have the right solution. The key to security log management is to collect the correct data so your security team can get better alerts to detect, investigate, and respond to threats faster.
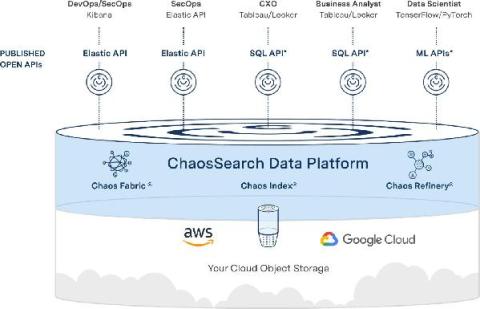
Cyber Defense Magazine Names ChaosSearch "Cutting Edge" in Cybersecurity Analytics
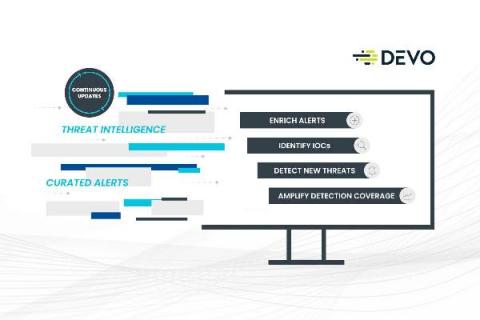
Security Operations, the Devo Next-Gen SIEM, Is Now Chock Full of Content
Devo has some big news for our customers, partners and prospects. We are pleased to announce the latest release of Devo Security Operations, which enables you to achieve full visibility without compromise, leverage real-time detections and enriched investigations, and maximize analyst productivity.
Executive Orders, Graylog, and You
In the last six months, multiple major cyber attacks have severely impacted hundreds of organizations in both the public and private sectors, and disrupted the daily lives of tens of thousands of their employees and customers.
Log Management and SIEM Overview: Using Both for Enterprise CyberSecurity
What is the Coralogix Security Traffic Analyzer (STA), and Why Do I Need It?
The wide-spread adoption of cloud infrastructure has proven to be highly beneficial, but has also introduced new challenges and added costs – especially when it comes to security. As organizations migrate to the cloud, they relinquish access to their servers and all information that flows between them and the outside world. This data is fundamental to both security and observability.