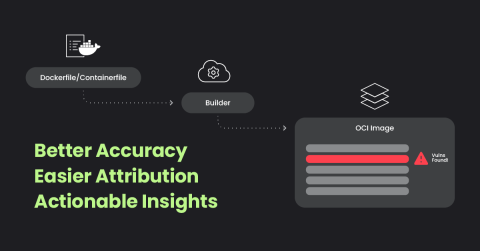
Sysdig Sage for Cloud Detection and Response
AI has supercharged cloud attacks - they are faster, more complex, and more sophisticated It's time for defenders to harness this powerful technology for good. Meet Sysdig Sage, the first AI cloud security analyst capable of multistep reasoning. Sysdig Sage goes beyond simple summarisation. It is context-aware. It is able to control the UI and move you across the platform. With Sysdig Sage on your side, investigating threats in real time is easier than ever.