Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Containers
CNCF Webinar: Critical DevSecOps considerations for Multicloud Kubernetes
CNCF Webinar: Getting started with container runtime security using Falco
Kubernetes Security
Secure Networking for Openshift
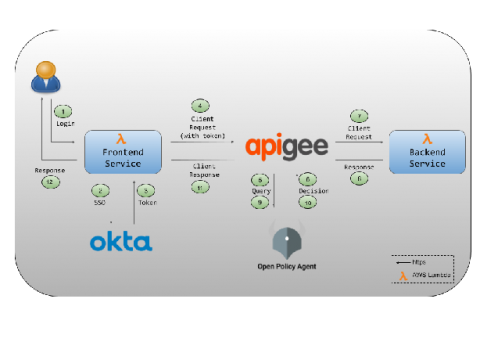
API Authorization at the Gateway with Apigee, Okta, and OPA (Part 2)
This is the second post in a two-part series about enforcing API authorization policies using Apigee, Okta and OPA. While the first post explained how to set up all three to work together, this post dives into detail on the policies that go along with the working code. The application we will be discussing is based on a hypothetical medical insurance provider Acme Health Care.
Kubernetes Q3-2020: Threats, Exploits and TTPs
Kubernetes has become the world’s most popular container orchestration system and is taking the enterprise ecosystem by storm. At this disruptive moment it’s useful to look back and review the security threats that have evolved in this dynamic landscape. Identifying these threats and exploits and being a proactive learner may save you a lot of time and effort…as well as help you retain your reputation in the long run.
Sysdig Boosts AWS Security with the First Automated Inline Scanning for Fargate
Automate Fargate image scanning
Discover how to automate AWS Fargate image scanning directly in your AWS environment and block vulnerabilities from reaching production, among other threats. AWS Fargate and ECS allow you to deploy containerized workloads quickly. Fargate is even more convenient, as you don’t have to take care of the infrastructure.
AWS threat detection using CloudTrail and Sysdig Secure
Implementing AWS threat detection with Sysdig Secure takes just a few minutes. Discover how to improve the security of your cloud infrastructure using AWS CloudTrail and Sysdig Cloud Connector. With the rise of microservices and DevOps practices, a new level of dangerous actors threatens the cloud environment that governs all of your infrastructure. A malicious or inattentive cloud API request could have a sizable impact on availability, performance, and last but not least, billing.