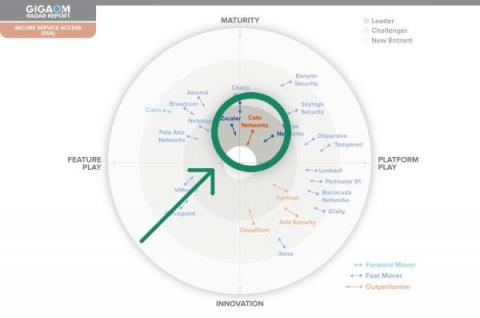
Cato SASE Cloud: A Two-Time Leader and Outperformer in GigaOm's Radar Report for Secure Service Access
In the ever-evolving world of cybersecurity, enterprises are constantly seeking the most effective solutions to secure their networks and data. GigaOm’s Radar Report for Secure Service Access, GigaOm’s term for SASE, provides a comprehensive look at the industry, and for the second consecutive year, names Cato Networks a “Leader” and “Outperformer.” The recognition points to Cato’s continuous commitment to innovation and improvement.