Who is responsible for bot management | Webinar series part-3
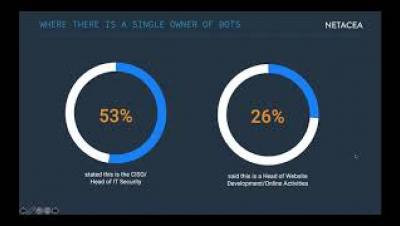
At Netacea, we wanted to know just how aware businesses are of bots and if they fully understand the threat to their organisation. Which roles are responsible, how confident are they in their bot mitigation strategies, and how well-placed is this confidence? We surveyed 200 enterprise businesses across travel, entertainment (including online gaming and streaming), e-commerce and financial services to get a broad picture of how bots are understood and protected against.