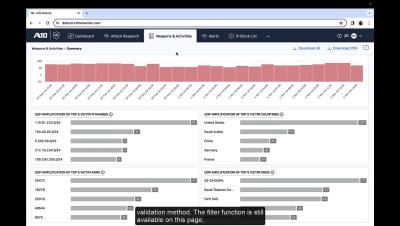
Meeting Growing Regulatory Requirements with A10 Networks
The European Union is tackling systemic risk in critical digital systems with two new regulations that come into force in the next 12 months. Watch to understand how to ensure your company's compliance with NIS2 and DORA regulations with the help of A10 Networks.