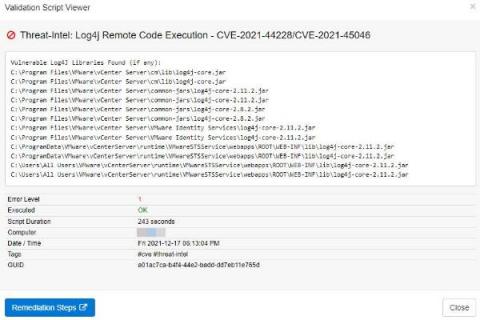
Devo's 2022 Cybersecurity Predictions: Part Three
In part two of our 2022 cybersecurity predictions series, Devo Security Engineering Director Sebastien Tricaud explained Web3 and new security testing trends. While cybersecurity tools and approaches are certainly evolving quickly, so are cybercriminals. Here are my insights on cyberthreats and attacks we should expect to see more of this year.