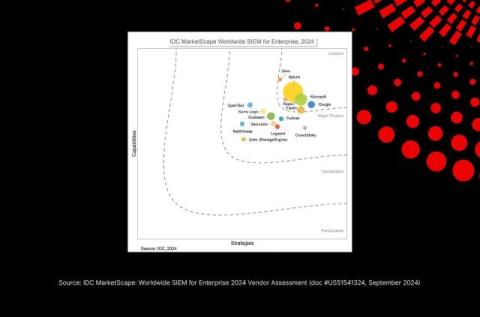
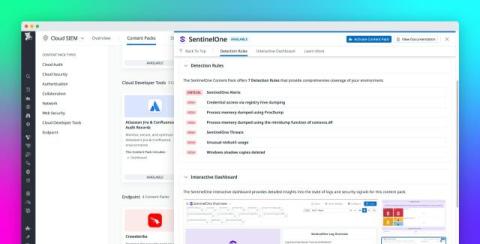
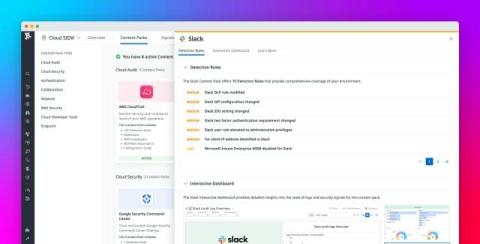
Assessing and Prioritizing Risk in Your Infrastructure
There are lots of hurdles to jump when trying to set up and maintain a SIEM. Preparing infrastructure and installing the software components, getting logs ingested into the system, parsing and normalizing those log messages properly, configuring alerts for detection, etc. These are all large tasks that require thoughtful planning and a lot of work to get right. But let’s say you’ve managed to clear all those hurdles…in that case, great job!!