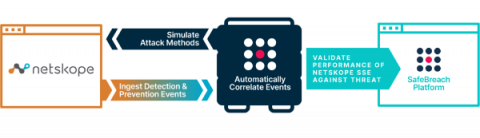
Validating and Optimizing your Security Service Edge Posture with SafeBreach and Netskope
Enterprise security operations teams find it increasingly difficult to maintain a hardened posture against advanced network and cloud threats. Given the rapid adoption of cloud platforms and software-as-a-service (SaaS) tools, cloud application traffic has overtaken web traffic to dramatically expand the attack surface. As a result, overreliance on traditional security controls can lead to increased blind spots, and control misconfigurations can create significant business risks.