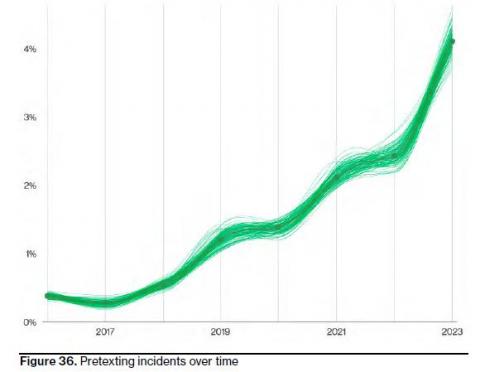
Verizon: Pretexting Now Tops Phishing in Social Engineering Attacks
The New Verizon DBIR is a treasure trove of data. As we covered here, and here, people are one of the most common factors contributing to successful data breaches. Let’s drill down a bit more in the Social Engineering section. They explained: "Now, who has received an email or a direct message on social media from a friend or family member who desperately needs money? Probably fewer of you. This is social engineering (pretexting specifically) and it takes more skill.