An Easy Guide to Understanding Risk Management and Quantification, 2
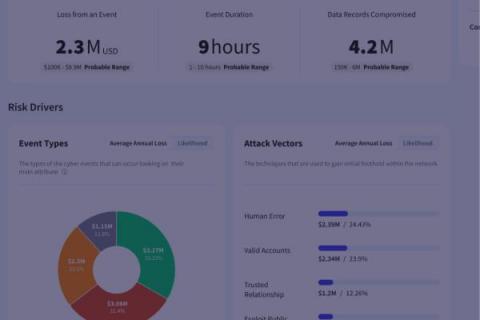
This is the second of a two part series on highlighting the power of cyber risk quantification, based on a webinar hosted by Kovrr’s Director of Product Management, Amir Kessler. Part two delves into the transformative potential of converting cyber risks from financial insights to actionable plans. Watch the full webinar here.