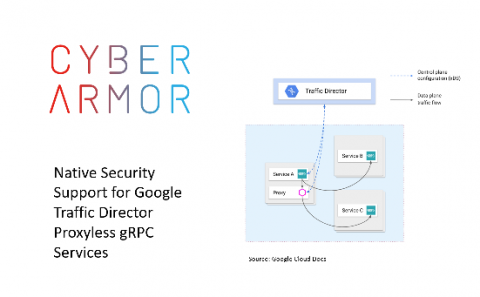
What makes ARMO customers immune - by design - against vulnerabilities like the recently discovered CVE-2020-14386?
CVE-2020-14386 is yet another severe vulnerability that was recently discovered in the Linux kernel. It reminds us that the fight against vulnerabilities is not over. This particular one allows a regular application to escalate its privileges and gain root access to the machine. Indeed, it sounds scary.