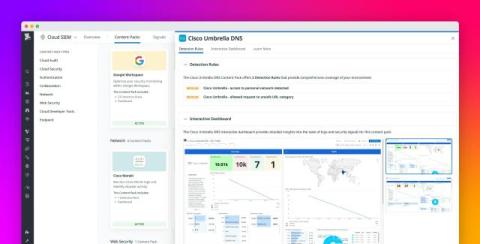
Monitor your Cisco Umbrella network logs with Datadog Cloud SIEM
Cisco Umbrella is a platform for monitoring and maintaining the DNS-layer security across your network. It monitors network activity and detects behavior like DNS hijacking, spoofing, and other attacks. It can then reroute or block potentially malicious requests before they reach endpoints. However, while Umbrella’s DNS-layer security blocks malicious domains, the sheer volume of DNS and proxy logs it generates can overwhelm security teams.